Cybersecurity is the activity of safeguarding vital systems and sensitive data against digital threats. Cybersecurity measures, also known as information technology (IT) security, are intended to prevent threats to networked systems and applications, whether they originate within or outside of a company.
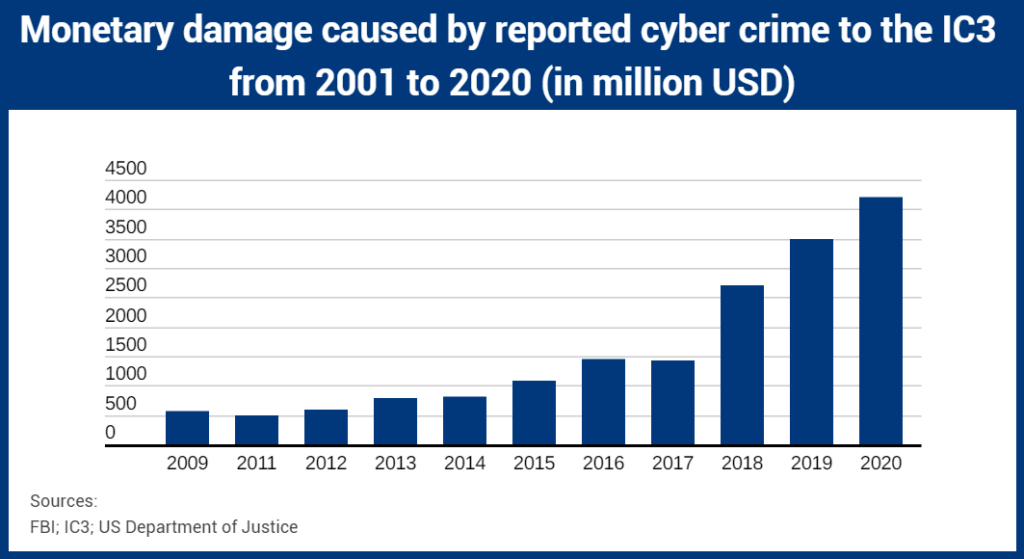
In 2020, the global average cost of a data breach was USD 3.86 million, with the US costing USD 8.64 million. These expenses include the costs of identifying and responding to the breach, the cost of downtime and lost revenue, as well as the long-term reputational damage to a company and its brand. Customers’ personally identifiable information (PII) — names, addresses, national identification numbers (e.g., Social Security numbers in the United States, fiscal codes in Italy — and credit card information — are targeted by cybercriminals, who then sell these records in underground digital marketplaces. Compromised PII frequently results in a loss of customer trust, regulatory fines, and possibly legal action.
The complexity of security systems caused by different technology and a lack of in-house knowledge can compound these expenses. However, organizations that implement a comprehensive cybersecurity strategy that is guided by best practices and automated through the use of advanced analytics, artificial intelligence (AI), and machine learning can combat cyberthreats more effectively and reduce the lifecycle and impact of breaches when they occur.
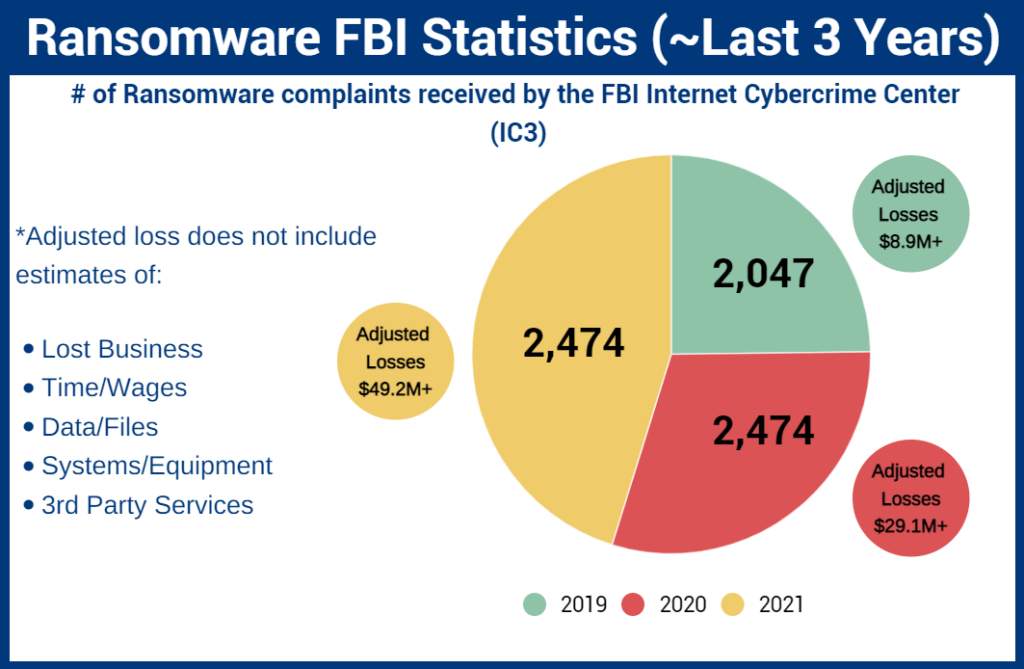
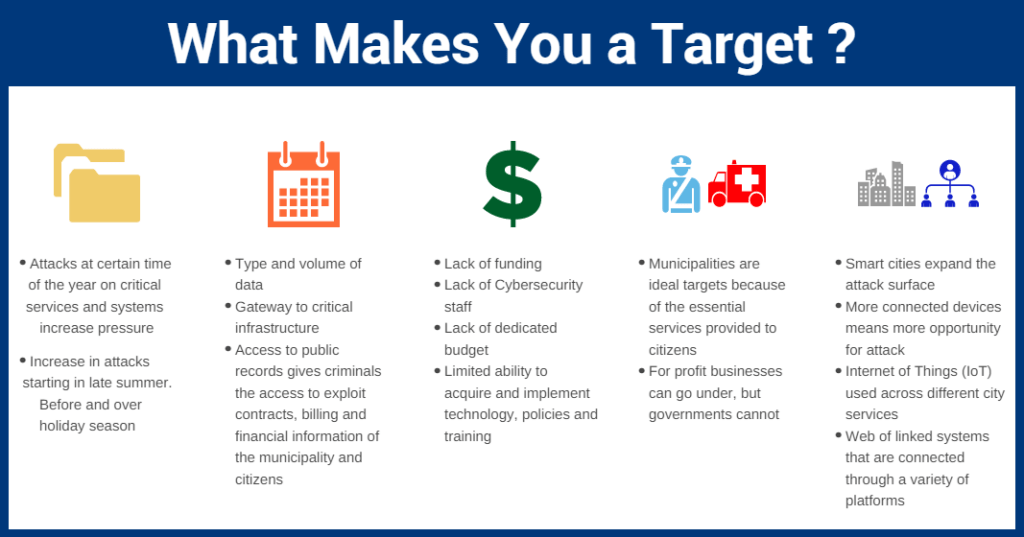
Boroughs and municipalities face cyber threats more than ever before. You have probably heard about the topic from an acquaintance or maybe even the victim of a successful cyber attack. Criminal actors find the local government sector to be an appealing target. Members who haven’t taken steps to prevent a breach are likely to experience some form of hack attempt sooner or later. Ransomware Plots, late adoption of Multi-Factor Authentication and other preventative measures, and even nation-state cyber attacks are creating a situation that renders your members more susceptible than ever. All of this is made worse by the fact that the market for cyber insurance is becoming increasingly competitive and scrutinizing the coverages it underwrites. It is essential that cities take preventative action and beef up their cyber security to lessen their cyber risk exposure.
Despite the efforts of cybersecurity professionals to plug security breaches, attackers are constantly seeking for new ways to avoid detection by IT, dodge protection measures, and exploit developing vulnerabilities. The most recent cybersecurity dangers are reinventing “existing” threats by leveraging work-from-home setups, remote access technologies, and new cloud services. Among the new threats are:
Malware refers to harmful software types such as worms, viruses, Trojans, and spyware that allow unauthorized access or cause computer damage. Malware attacks are becoming increasingly “fileless,” aiming to avoid detection measures such as antivirus software that scan for harmful file attachments.
Ransomware is a sort of software that encrypts files, data, or systems and threatens to delete or destroy the data – or expose private or sensitive material – unless a ransom is paid to the cybercriminals who began the attack. Recent ransomware attacks have targeted state and municipal governments, which are easier to compromise than organizations and are under pressure to pay ransoms in order to restore critical programs and websites used by citizens.
Phishing is a type of social engineering in which people are duped into disclosing PII or sensitive information. Phishing scams involve emails or text messages that look to be from a reputable company and request sensitive information such as credit card information or login information. The FBI has reported an increase in pandemic-related phishing, which has been linked to the development of remote labor.
Insider threats might include current or former workers, business partners, contractors, or anyone who has previously had access to systems or networks who abuses their access permissions. Traditional security solutions, such as firewalls and intrusion detection systems, which focus on external threats, may be blind to insider risks.
A DDoS assault tries to bring down a server, website, or network by flooding it with traffic from numerous synchronized systems. DDoS assaults disrupt enterprise networks by using the simple network management protocol (SNMP), which is utilized by modems, printers, switches, routers, and servers.
An APT involves an attacker or a group of intruders infiltrating a system and remaining undiscovered for a lengthy period of time. The invader leaves networks and systems intact in order to eavesdrop on company activity and take important data without triggering defensive countermeasures. An example of an APT is the recent Solar Winds penetration of US federal computers.
SOME WAYS TO PREVENT CYBER ATTACKS
ON GOVERNMENT AGENCIES
Putting your data and information on a dedicated cloud server will help ensure that your data is neatly catalogued, organized and safe on a single computer at your work site. We can allow chosen individuals access to these cloud servers through a laptop or a phone no matter where they are. Having cyber security specialists that will test and make sure that your systems are up to date and strong enough to defend any attempted breaches makes all the difference. Proactive IT security measures include network components such as: managed firewalls, anti-virus & anti-malware, content filtering, spam filtering, dark web monitoring, etc. we tell our clients to always consider proactive security measures as the first line of defense against potential threat vectors such as DDOS attacks, viruses, and malware. Infradapt can help with all that, and also put in place any required additional measures such as multi authentication factor, malware protection and even security awareness training. We can also Assist you with your most critical applications such as estimating, accounting, project management, document management, scale management, and ERP systems. management, document management, scale management, and ERP systems. Our industry specific cyber-security certification helps us make sure to give the best assistance possible within given guidelines.
cyber security