At Infradapt we live by a preventive approach to cyber security. Each end user that owns, uses, relies on, or manages information and information systems must fully understand their specific security responsibilities. This includes concepts of ownership of the information and custody of the information and the role individuals have in protecting information they own, information provided to them or information they may come into contact with. We share (teach) best practices and techniques to avoid:
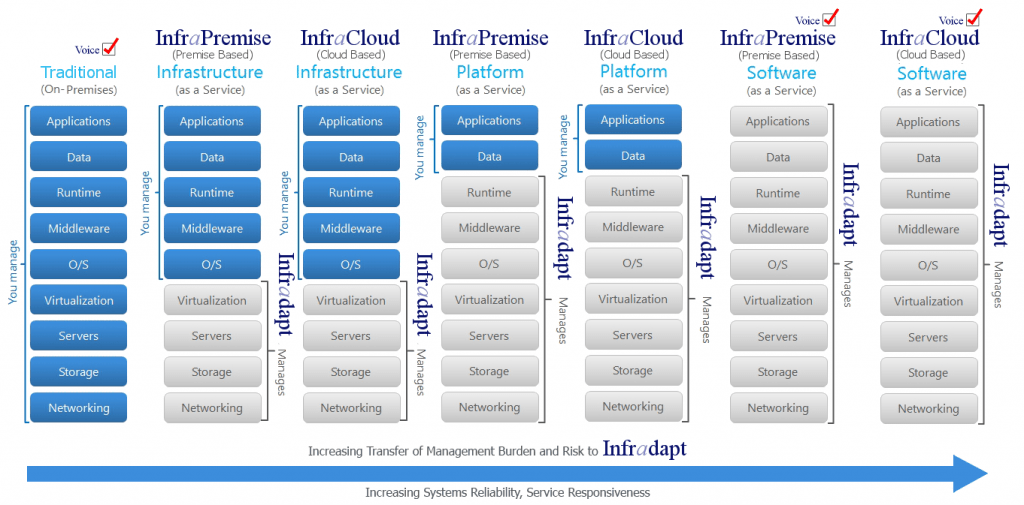
In addition to traditional IT offers, Infradapt developed InfraCloud our Cloud-Based Fixed Rate offering and InfraPremise our Premise-Based Fixed Rate and comprehensive offers that include all hardware, software, and services to satisfy your specific needs.
Unlike other companies that only broker or resell third party cloud services, Infradapt manages our own distributed cloud based infrastructure made available to all of our customers, in addition to third party public cloud services.
The more Infradapt infrastructure services you use, the more you transfer the risk associated with IT to Infradapt.
InfraCloud is fully protected with: Redundant Internet, Fire Suppression, Redundant Power, Redundant HVAC, Physical Security, Data Backup, Dust Control and much more.
Fixed Rate Cloud-Based Offers
Fixed Rate On-Premise Based Offers
Fixed Rate Total Support to Cloud, Premise or Hybrid Offers
All Inclusive Service and Support
IT Support
Telecom Support
Proactive Maintenance
Virtual CIO
Hassle Free Vendor Management
Cyber Security Management
Backup and Disaster Recovery
Risk Assessment / Remediation Process
Staff Training / Process Implementation
24 / 7 Monitoring and Incident Response
Gap Analysis / Remediation Report
Compliance Documentation
Hyper Backup Protection
24 / 7 / 365 Unlimited Helpdesk
All Hardware Included
Trouble-Ticketing System Included
Smartphone Included
Office 365 Software Plan Included
Business PBX Included
Private Cloud Included
Managed IT Services Included
Ransomware Protection
Real-Time Cloud Replication
Hyper Backup Protection
High Availability Architecture
Voice High Availability
Quickest Point-in-Time Restores
24 / 7 / 365 Monitoring and Support
Hosted, Premise or Hybrid
Trouble-Ticketing System Included
Unlimited IVRs, VMs, and Queues
Skype and Salesforce Integration
Call Center / Contact Center Ready
High Availability Included
Telecom Management Included
No Capital Investment
Quick Provisioning
Flexibility and Elasticity
Private Cloud, Share Nothing
24 / 7 / 365 Monitoring and Alert
Data Bunker Facility
Redundant High-Bandwidth and Power
Outdated technology limiting your productivity?
In need of more organized business infrastructure?
Feeling limited by the restrictions of your current systems?
No matter the issues your company faces, when it comes to technology and information, Infradapt is here to help. Start by scheduling your free consultation, and we’ll work together to determine how Infradapt can help keep your business running smoothly, efficiently, and productively.
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These cyber attacks are usually aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting normal business processes.
Cyber liability protection is a type of insurance designed to cover businesses for financial losses resulting from cyber incidents and security breaches. This can include costs associated with data breaches, recovery of lost data, legal fees, and expenses related to identity theft or network security liabilities.
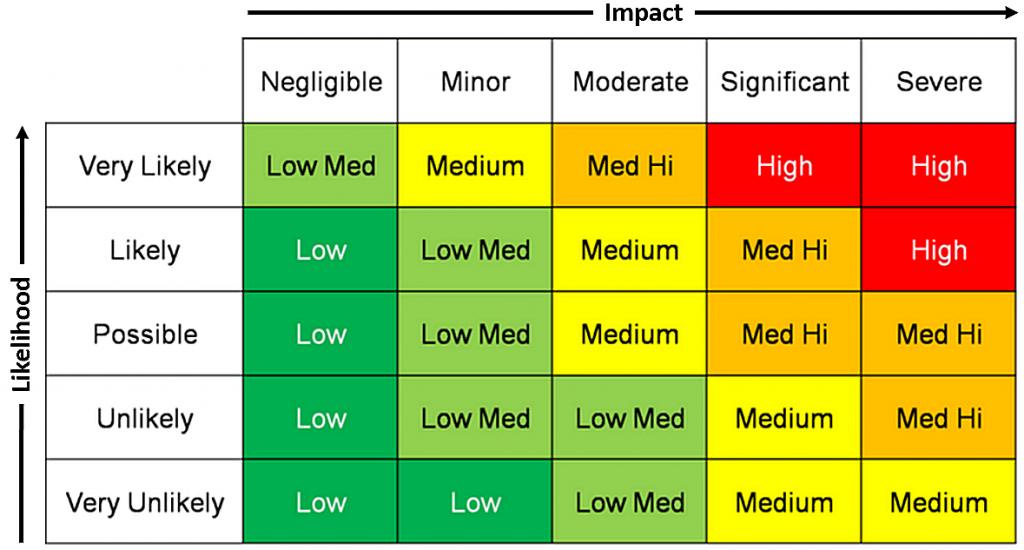
Cybersecurity is crucial for businesses to protect their sensitive data, maintain customer trust, and ensure the continuity of their operations. A breach can result in significant financial losses, damage to reputation, and legal consequences.
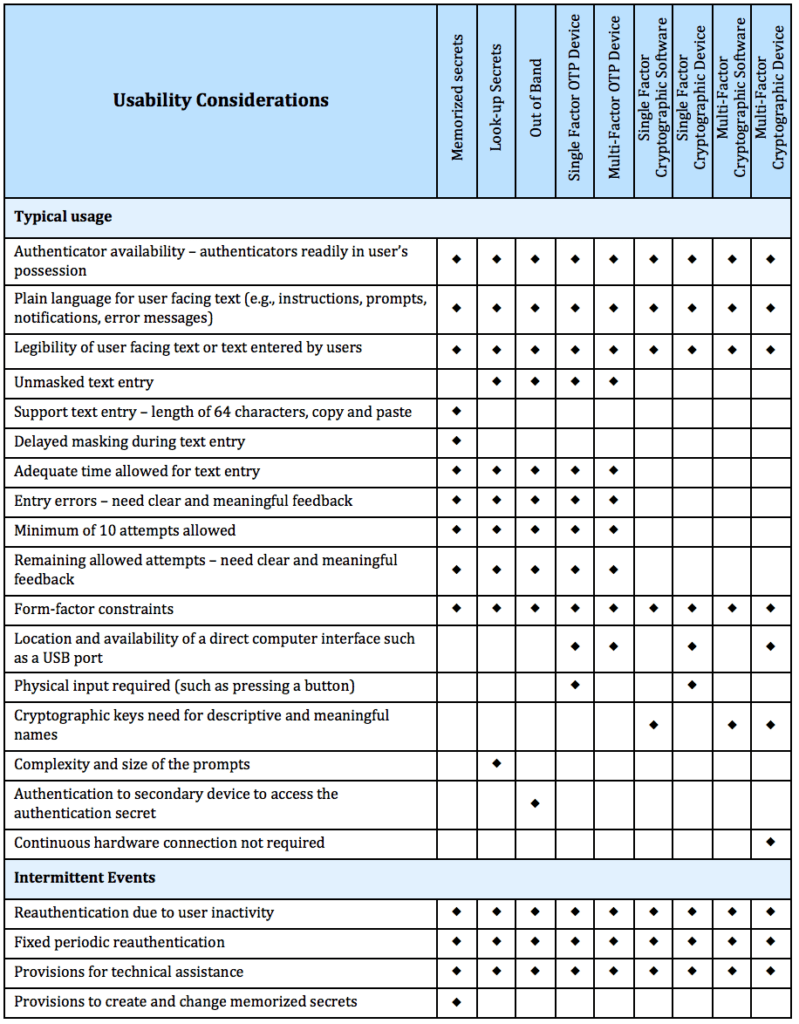
Infradapt offers comprehensive cybersecurity services that include regular monitoring, threat detection and response, firewall and antivirus management, security assessments, and employee training to enhance your organization’s overall security posture.
Common cyber threats include phishing attacks, ransomware, malware, social engineering, insider threats, and DDoS (Distributed Denial of Service) attacks.
Businesses can improve cybersecurity by implementing a robust security framework, conducting regular security assessments, training employees on security best practices, updating and patching systems regularly, and employing advanced threat detection and response measures.
No, cyber liability insurance is not a substitute for robust cybersecurity measures. It is designed to mitigate financial risks associated with cyber incidents, not prevent them. Businesses need both strong cybersecurity defenses and cyber liability protection to manage their cyber risk effectively.