In a competitive market like Philadelphia, business continuity is everything. From law firms in Center City to manufacturers in the surrounding suburbs, your operations depend on the security of your endpoints. Today's threats bypass traditional antivirus with ease, targeting employee laptops and critical servers to steal data and launch ransomware attacks. Infradapt provides a premier managed endpoint protection service built for the pace of Philadelphia business. We act as your dedicated security team, deploying advanced EDR/XDR technology and 24/7 monitoring to protect every device, ensuring your data is secure and your workforce stays productive.
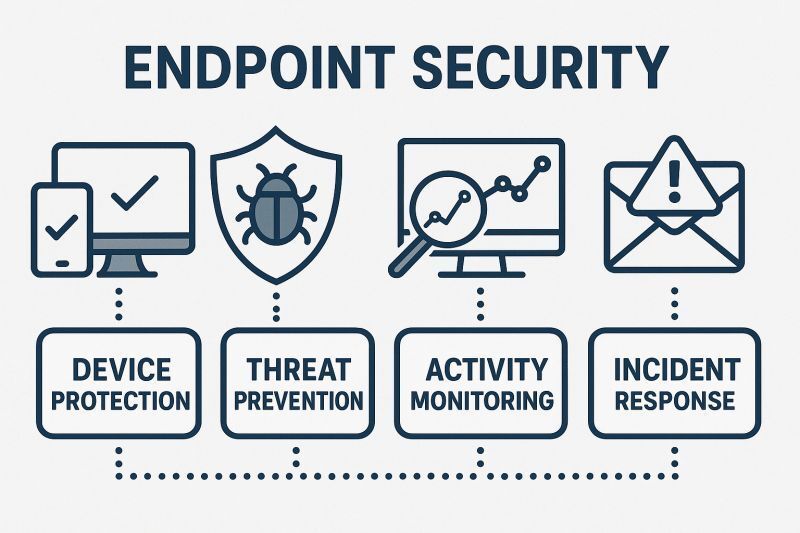
Modern endpoint security goes beyond legacy antivirus. It includes:
Infradapt blends these layers with policy hardening, encryption, and patch/vulnerability management—delivered as a managed service.
Our strategy applies prevention first (hardening), real-time detection (EDR/XDR), and rapid response (automated isolation and rollback), backed by a 24×7 SOC.
Bundle with Cyber Security, Managed IT Services, and Cloud Backup & BCDR for layered protection.
Controls map to common frameworks including CJIS, HIPAA, PCI-DSS, FERPA, NIST 800-53/171 (Zero Trust aligned), and others. Our team includes compliance specialists who align endpoint policies and audit evidence with agency requirements.
Tip: If your AV doesn’t record endpoint telemetry, investigate XDR for earlier, richer detections.
Every organization is different. We tailor endpoint protection around your fleet, workflows, and compliance needs, then handle deployment and ongoing monitoring so your team stays focused on the work that matters. Start with a free consultation from an Infradapt endpoint security expert.
Think of an MSP as your on-demand, expert IT department. Instead of hiring your own staff, you partner with us to proactively manage, maintain, and support all your technology—from computers to security—for a predictable monthly fee.
For many businesses, an MSP is more cost-effective. You get an entire team of diverse experts for less than the cost of one senior employee. We provide 24/7 coverage, so you're never left unsupported on vacations or sick days.
We save you money by preventing expensive problems like downtime or data loss before they happen. Our flat-fee model gives you a predictable budget and lets your team focus on their actual jobs instead of wasting time on IT issues.
You and your employees get access to our dedicated helpdesk. Just give us a call or send an email, and a technician will start working on your issue immediately. No problem is too small!
Getting started is simple. We begin with an assessment of your current technology, then deploy our management tools silently in the background. We handle the entire transition with a clear plan to ensure minimal disruption to your workday.
Deployment is typically completed within 4 to 8 weeks. Our team assists with a phased, silent rollout to ensure a smooth transition without disrupting your business operations.
We use multiple layers of security to protect your data. More importantly, we implement a robust backup and disaster recovery solution. We automatically back up your critical files so if anything happens, we can restore your data quickly.
Yes. Our modern security solution is a "next-gen antivirus" that includes EDR/XDR capabilities, making traditional antivirus obsolete. We manage a phased rollout to ensure a seamless transition.
EDR focuses on threats at the endpoint (laptops, servers). XDR is the next step, integrating data from other sources—like email, cloud, and your network—to see the bigger picture and stop complex attacks.
We use advanced behavioral analysis and machine learning, not just old-fashioned signatures. This allows us to detect suspicious activity patterns indicative of new malware, ransomware, and fileless attacks.
When our SOC confirms a threat, we immediately contain it by isolating systems, neutralize the malicious activity, and provide a full report on what happened and how to prevent it in the future.
Absolutely. Our Security Operations Center (SOC) can remotely isolate an endpoint in seconds to prevent a threat from spreading. We then neutralize the threat and guide the remediation process.
Our platform helps you meet compliance requirements (e.g., PCI-DSS, HIPAA, GDPR) by providing continuous monitoring, detailed security logs, and audit-ready reports on security controls and incident response activities.
Yes. Our agents protect and monitor your devices anywhere your employees are—in the office, at home, or on the road—ensuring constant protection for your remote workforce.
No. The security agent is lightweight and optimized for minimal performance impact. It operates silently in the background, so your team won't notice it during their day-to-day work.
We provide full coverage for Windows, macOS, and major Linux distributions for both servers and workstations, plus support for iOS and Android via MDM/UEM integration.
We use staged rollouts and create specific security policies, such as application allow-listing with exceptions that are validated in a pilot group before company-wide deployment.
We provide monthly executive summaries covering key metrics like incidents blocked, mean time to respond (MTTR), patch compliance, exposure trends, and prioritized actions for risk reduction.
Learn More
Contact an Infradapt Solutions Specialist online or call 1-800-394-2301 to explore how Infradapt’s endpoint protection can strengthen your security program.